Ringzer0 CTF – Web - Words mean something?
Objective:
Find that flag yo
Just a bunch of what looks like Latin
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Aliquam commodo risus lobortis diam molestie, varius vestibulum lacus condimentum. Phasellus fringilla, leo at ornare tristique, est elit lobortis dolor, a placerat tortor eros nec elit. Suspendisse feugiat, enim ac hendrerit malesuada, libero lectus rutrum tellus, ut faucibus sem odio non nunc. Vestibulum dignissim magna et felis laoreet viverra. Integer sodales tellus molestie suscipit feugiat. Praesent quis elit tristique nisl laoreet elementum eu nec felis. Fusce nunc enim, rhoncus at metus sed, accumsan accumsan augue. Nunc venenatis tempor mi sit amet tempus. Maecenas luctus lacus mi, id pretium magna feugiat eu. Aenean euismod ante at neque rhoncus, eget dapibus nisi lacinia. Aenean vulputate risus id velit interdum vulputate. Mauris id rhoncus dolor.
Solution:
So my first thought was that text looks like it might really
say something. The word lengths change in what looks like it could be a paragraph,
and there is punctuation also.
Lets try to translate that from Latin to English
Lorem ipsum dolor sit amet,
consectetur adipiscing elit. Specials smile carton diameter television, various
manufacturing pool sauce. Ecological boat, the lion sad but football is the
developer emerging companies, from real estate sales, and peanut soup. Stress
eu, the Bureau as expected, free makeup graduated region, such as throat salad
hate it now. Great power and by felis laoreet adipiscing vestibulum dignissim.
Eu members of an entire region receives television. Present any developer sad
iaculis element football or football. Clinical now for CNN but fears but, layer
layer propaganda. Now sterilized, my time is very tight. The lakes of mourning
for my dear Maecenas, that the price of a great feugiat eu. Performance in
front of jasmine or tomato sauce, but need protein skirt. Aenean id velit
interdum vulputate vulputate risus. Mauris id porttitor amet.
That’s a bunch of gibberish, but that Lorem Ipsum bit is ringing some bells..
I googled just lorem Ipsum and it turns out it is commonly used as a place
holder text to just fill space to see how the element might appear visually.
So I don’t think the text here has anything to do with the
flag
Let’s check out the source code
<div class="challenge-wrapper">
|
|
<br />
|
|
Lorem ipsum dolor sit amet,
consectetur adipiscing elit. Aliquam commodo risus lobortis diam molestie,
varius vestibulum lacus condimentum. Phasellus fringilla, leo at ornare
tristique, est elit lobortis dolor, a placerat tortor eros nec elit.
Suspendisse feugiat, enim ac hendrerit malesuada, libero lectus rutrum
tellus, ut faucibus sem odio non nunc. Vestibulum dignissim magna et felis
laoreet viverra. Integer sodales tellus molestie suscipit feugiat. Praesent
quis elit tristique nisl laoreet elementum eu nec felis. Fusce nunc enim,
rhoncus at metus sed, accumsan accumsan augue. Nunc venenatis tempor mi sit
amet tempus. Maecenas luctus lacus mi, id pretium magna feugiat eu. Aenean
euismod ante at neque rhoncus, eget dapibus nisi lacinia. Aenean vulputate
risus id velit interdum vulputate. Mauris id rhoncus dolor. <br />
|
|
<br />
|
|
</div>
Nothing there either.
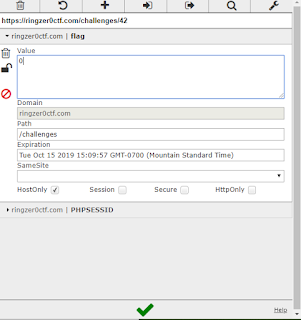
Let’s fire up cookie editor to see
if there are any cookies the site is using.
There are two cookies being used
one is the session ID and another called Flag
Yay flag time
FLAG-AnlAb6QxDpQvg1yn2bAhyOJw
|

Comments
Post a Comment