HacktheBox - Delivery - Retired

As per my normal, I'll start off with a quick scan using threader600, followed by a more indepth scan based on the results.
Threader6000 recommends the following Nmap scan:
************************************************************
nmap -p22,80,8065 -sV -sC -T4 -Pn -oN 10.10.10.222 10.10.10.222
************************************************************
Would you like to run Nmap or quit to terminal?
------------------------------------------------------------
1 = Run suggested Nmap scan
2 = Run another Threader6000 scan
3 = Exit to terminal
------------------------------------------------------------
Option Selection: 1
nmap -p22,80,8065 -sV -sC -Pn -T4 -oN 10.10.10.222 10.10.10.222
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-15 18:23 EDT
Nmap scan report for 10.10.10.222
Host is up (0.059s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:40:fa:85:9b:01:ac:ac:0e:bc:0c:19:51:8a:ee:27 (RSA)
| 256 5a:0c:c0:3b:9b:76:55:2e:6e:c4:f4:b9:5d:76:17:09 (ECDSA)
|_ 256 b7:9d:f7:48:9d:a2:f2:76:30:fd:42:d3:35:3a:80:8c (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome
8065/tcp open unknown
| fingerprint-strings:
| GenericLines, Help, RTSPRequest, SSLSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Accept-Ranges: bytes
| Cache-Control: no-cache, max-age=31556926, public
| Content-Length: 3108
| Content-Security-Policy: frame-ancestors 'self'; script-src 'self' cdn.rudderlabs.com
| Content-Type: text/html; charset=utf-8
| Last-Modified: Thu, 15 Apr 2021 22:26:43 GMT
| X-Frame-Options: SAMEORIGIN
| X-Request-Id: nz5ygru6uiygmcympdoghj41fa
| X-Version-Id: 5.30.0.5.30.1.57fb31b889bf81d99d8af8176d4bbaaa.false
| Date: Thu, 15 Apr 2021 22:28:32 GMT
| <!doctype html><html lang="en"><head><meta charset="utf-8"><meta name="viewport" content="width=device-width,initial-scale=1,maximum-scale=1,user-scalable=0"><meta name="robots" content="noindex, nofollow"><meta name="referrer" content="no-referrer"><title>Mattermost</title><meta name="mobile-web-app-capable" content="yes"><meta name="application-name" content="Mattermost"><meta name="format-detection" content="telephone=no"><link re
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Date: Thu, 15 Apr 2021 22:28:32 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8065-TCP:V=7.91%I=7%D=4/15%Time=6078BCF7%P=x86_64-pc-linux-gnu%r(Ge
SF:nericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20t
SF:ext/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x
SF:20Request")%r(GetRequest,DF3,"HTTP/1\.0\x20200\x20OK\r\nAccept-Ranges:\
SF:x20bytes\r\nCache-Control:\x20no-cache,\x20max-age=31556926,\x20public\
SF:r\nContent-Length:\x203108\r\nContent-Security-Policy:\x20frame-ancesto
SF:rs\x20'self';\x20script-src\x20'self'\x20cdn\.rudderlabs\.com\r\nConten
SF:t-Type:\x20text/html;\x20charset=utf-8\r\nLast-Modified:\x20Thu,\x2015\
SF:x20Apr\x202021\x2022:26:43\x20GMT\r\nX-Frame-Options:\x20SAMEORIGIN\r\n
SF:X-Request-Id:\x20nz5ygru6uiygmcympdoghj41fa\r\nX-Version-Id:\x205\.30\.
SF:0\.5\.30\.1\.57fb31b889bf81d99d8af8176d4bbaaa\.false\r\nDate:\x20Thu,\x
SF:2015\x20Apr\x202021\x2022:28:32\x20GMT\r\n\r\n<!doctype\x20html><html\x
SF:20lang=\"en\"><head><meta\x20charset=\"utf-8\"><meta\x20name=\"viewport
SF:\"\x20content=\"width=device-width,initial-scale=1,maximum-scale=1,user
SF:-scalable=0\"><meta\x20name=\"robots\"\x20content=\"noindex,\x20nofollo
SF:w\"><meta\x20name=\"referrer\"\x20content=\"no-referrer\"><title>Matter
SF:most</title><meta\x20name=\"mobile-web-app-capable\"\x20content=\"yes\"
SF:><meta\x20name=\"application-name\"\x20content=\"Mattermost\"><meta\x20
SF:name=\"format-detection\"\x20content=\"telephone=no\"><link\x20re")%r(H
SF:TTPOptions,5B,"HTTP/1\.0\x20405\x20Method\x20Not\x20Allowed\r\nDate:\x2
SF:0Thu,\x2015\x20Apr\x202021\x2022:28:32\x20GMT\r\nContent-Length:\x200\r
SF:\n\r\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConten
SF:t-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n
SF:400\x20Bad\x20Request")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r
SF:\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close
SF:\r\n\r\n400\x20Bad\x20Request")%r(SSLSessionReq,67,"HTTP/1\.1\x20400\x2
SF:0Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nCon
SF:nection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(TerminalServerCookie
SF:,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;
SF:\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request"
SF:);
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 94.57 seconds
------------------------------------------------------------
|
Looks like we have nginx running
Let's add 10.10.10.222 delivery.htb to our hosts file.

Not much here, but there is a reference to helpdesk.delivery.htb. Let's add that to our /etc/hosts

Looks like a helpdesk ticketing site running OSticket and open source ticketing platform.
There was also another port which we should check out. 8065

Mattermost

Let's try to register an account.

Looks like you need email to register an account, since this is HTB… and their boxes don't talk to the outside world… this doesn't look like the path in for us.
Let's head back over to the helpdesk. It looks like technicians have a separate login portal

Let's try to register a user account

Crap that needs email verification too….. So that is not our path.
But we can create tickets as a guest.

We get a ticket created response as well as a ticket number
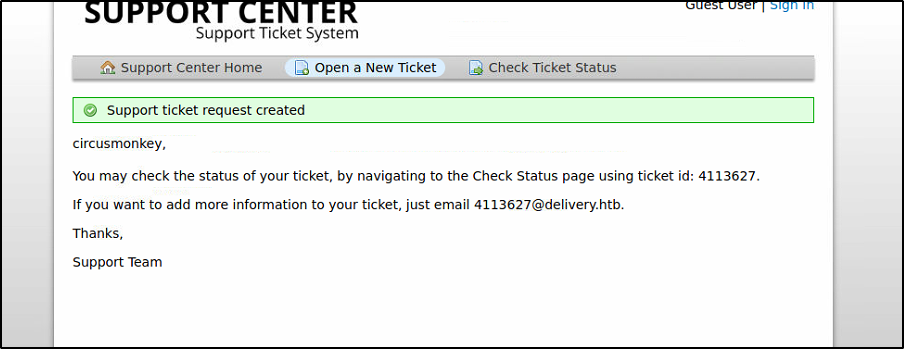
We can view the status of our ticket as guests.

This is interesting.
https://www.exploit-db.com/exploits/49441
Os-ticket has an SSRF that you can use to get the system to download files.

I did
In the text(html) editor
And you can see here the box reached out to download it.

But how to get it to run what it downloads?
http://delivery.htb:8065/do_verify_emailtoken=c4ezcpibi768h5z7tjt4nmq53kyoxpykx5hzq5nf1935ojedeg7fixkdhumuuwx4&email=4113627%40delivery.htb
On the mattermost page it says when we have our delivery.htb email setup we can set up an account… And when we created that guest ticket it created a @delivery.htb email box for adding to the ticket.
Let's try to register for a mattermost account using the email address created by the os ticket.

We got a registration ticket. If we copy the link out to our browser it lets us register and login with the mattermost account we created!!!
Thanks OS ticket!

Let's poke around here and see what we might find.
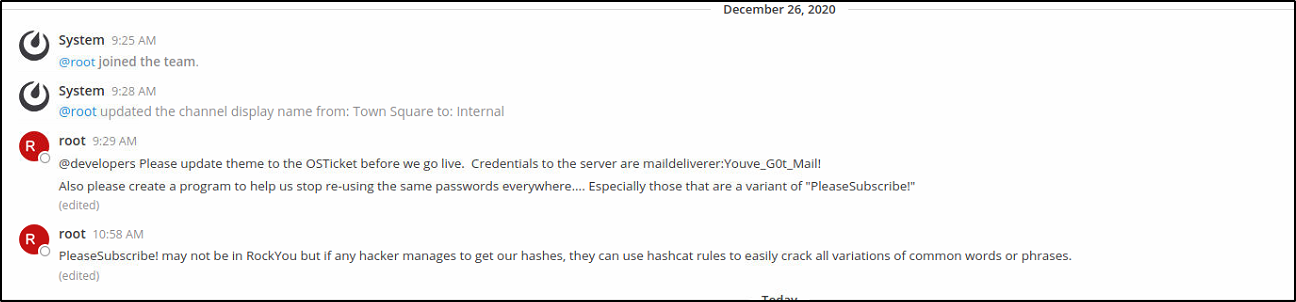
Looks like we have some hints here …
A message about the passwords being a variant of pleasesubscribe!
And another about what looks like the creds for SMTP function in os ticket.
Well just for grins and giggles I the creds listed for the admin os ticket portal…
maildeliverer:Youve_G0t_Mail!

New things to dig into… let's see if we can find a path to execution from this data.
Guess what we can also SSH with these creds.. No need to try and get a webshell
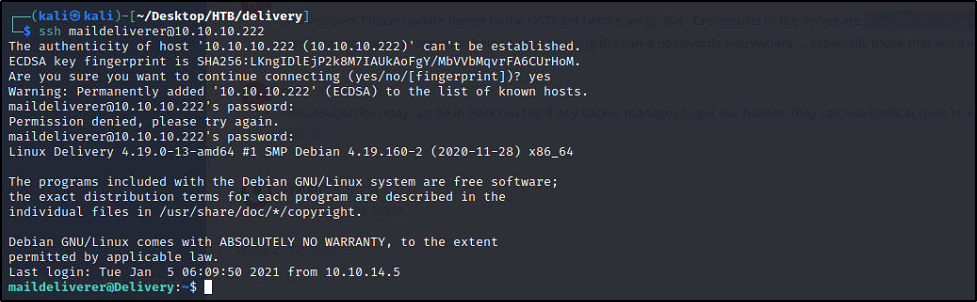
We can get the user flag from here..
I spent some time doing recon on the box pulled out the /etc/passwd file and something jumped out.
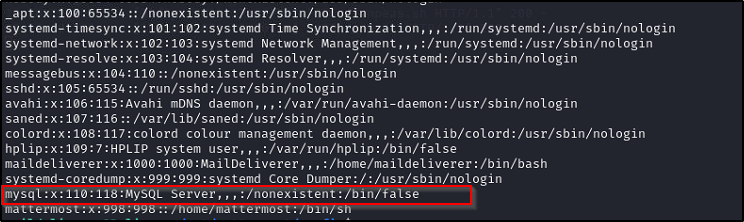
Mysql is here. I tried logging in as root with the password we used for the SSH session, no dice
Poking around in the /opt/mattermost/config folder I found this config.json file

"DataSource": "mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost?charset=utf8mb4,utf8\u0026readTimeout=30s\u0026writeTimeout=30s",
Well that looks like mysql creds
mmuser:Crack_The_MM_Admin_PW

It sure is, our clue says to find a password. And remember we found a clue about using rules and the default of PleaseSubscrbe…
Let's see if we can find a user table
Use
To see there is a mattermost Database.
Use mattermost;
To see the tables.

That looks like a hash of root's password…..
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO
$2a$10$ tells its possible a bcrypt
So let's start easy and just use some hashcat masks to add some digits to what the "Default" password is.
?d = is a mask for numerals
So PleaseSubscribe!?d?d
Would try all the numbers 0-9 appended twice to the end of the default password.
So our command would look like.
hashcat64.exe -m 3200 C:\Users\aaron\Desktop\delivery.txt -a 3 PleaseSubscribe!?d?d |
We got it

PleaseSubscribe!21
Let's see if we can su as root with that password.
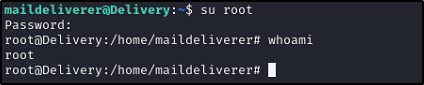
Sure can, just need to grab that flag!


Comments
Post a Comment